Information Security and Privacy: 26th Australasian Conference, ACISP 2021, Virtual Event, December 1?3, 2021, Proceed
(税込) 送料込み
商品の説明
商品情報
Information Security and Privacy: 26th Australasian Conference, ACISP 2021, Virtual Event, December 1?3, 2021, Proceedings (Lecture Notes in Computer Science)
12919円Information Security and Privacy: 26th Australasian Conference, ACISP 2021, Virtual Event, December 1?3, 2021, Proceed家具、インテリアカーペット、ラグ、マットACISP 2021 - The 26th Australasian Conference on Information
商品コード:16065985261
サイズ:6.2" X 9.2"
カラー:Sd-mo20。
主な素材:ポリエステル100%&コーラルフリース。
サイズ:6.2フィート×9.2フィート(190cm×280cm)(74.8インチ×110インチ)。
とても柔らかく快適: このモダンなエリアラグは通気性のあるポイントプラスチックで機械織られており、滑り止めの底でラグが滑り落ちるのを防ぎます。 超ソフトで快適で肌に優しいコーラルフリース 抜け毛が信じられないほどソフトな感触です。 安全を確保し、健康に良い。
お手入れ簡単で速乾: 強力な吸水力、お手入れ簡単、ほぼ毛抜けないラグ。お手入れ簡単、速乾性、非常に耐久性、ノンスリップ、洗濯機で洗えます。 ポータブルラグとInformation Security and Privacy: 26th Australasian Conference
ACISP 2021 - The 26th Australasian Conference on Information
Information Security and Privacy: 26th Australasian Conference
ACISP 2021 - The 26th Australasian Conference on Information
ACISP 2021 - The 26th Australasian Conference on Information
ACISP 2021 - The 26th Australasian Conference on Information
ACISP 2021 - The 26th Australasian Conference on Information
ACISP 2021 - The 26th Australasian Conference on Information
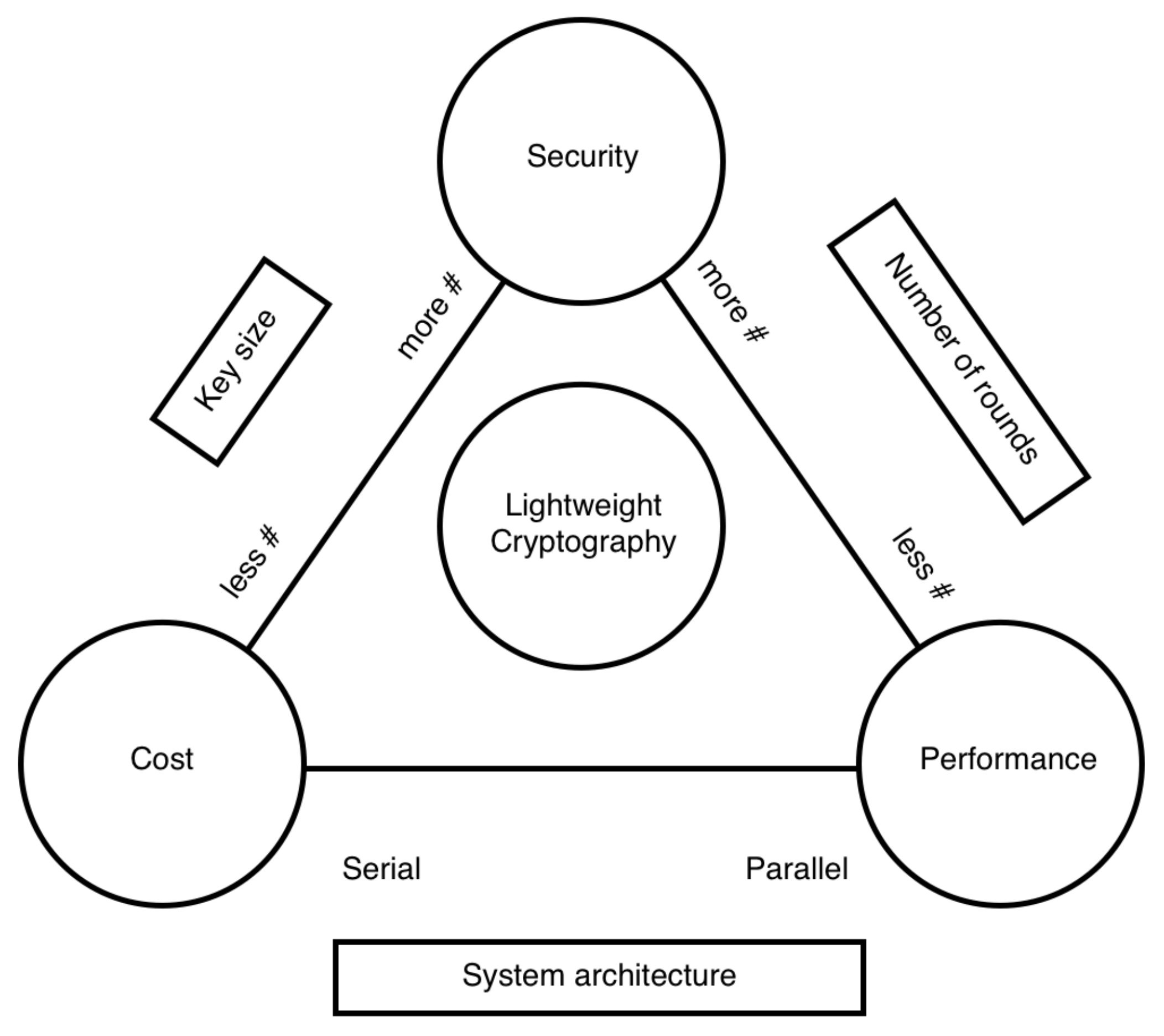
Electronics | Free Full-Text | A Review of the NIST Lightweight
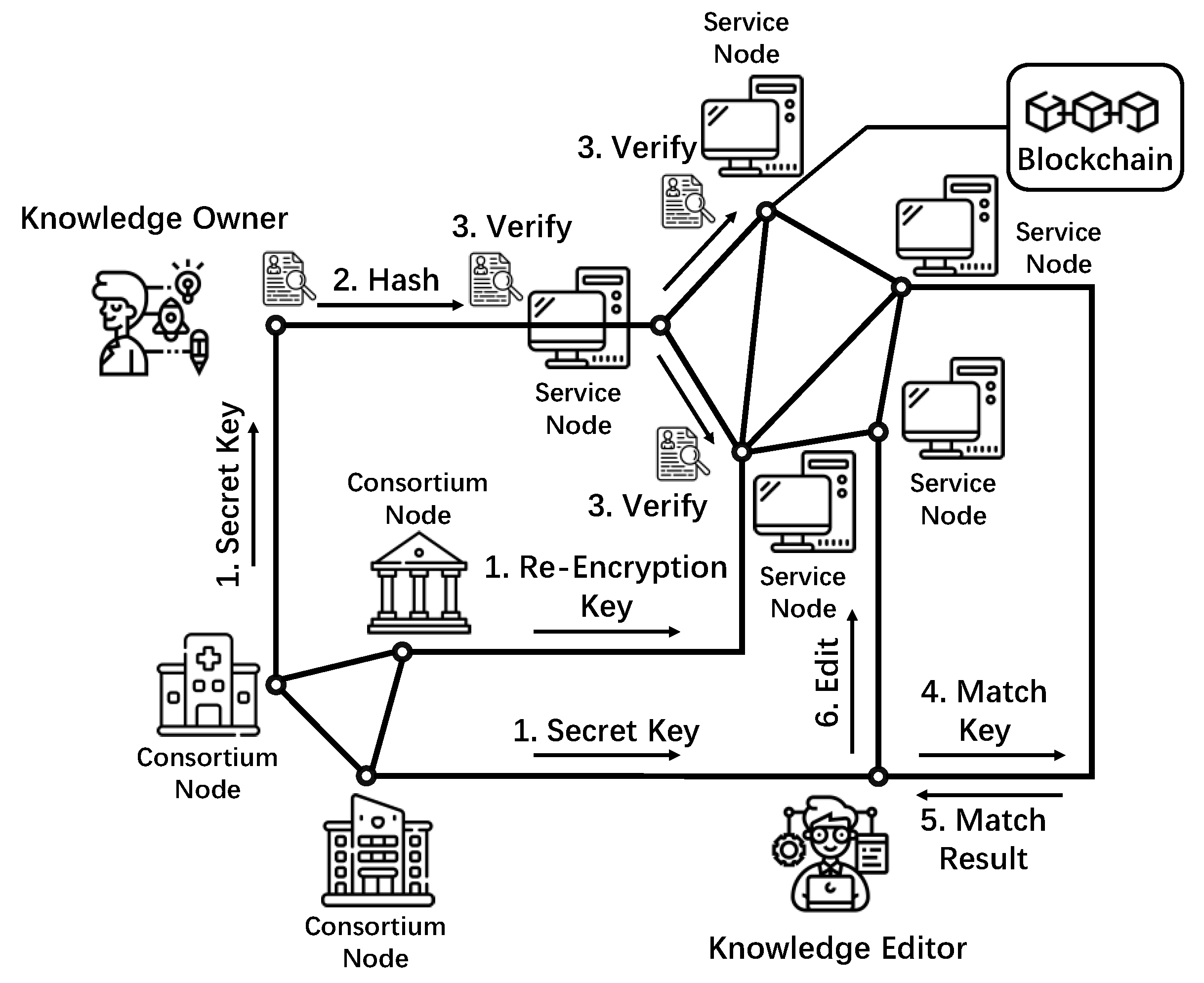
Electronics | Free Full-Text | PIRB: Privacy-Preserving Identity
Security Analysis of End-to-End Encryption for Zoom Meetings⋆
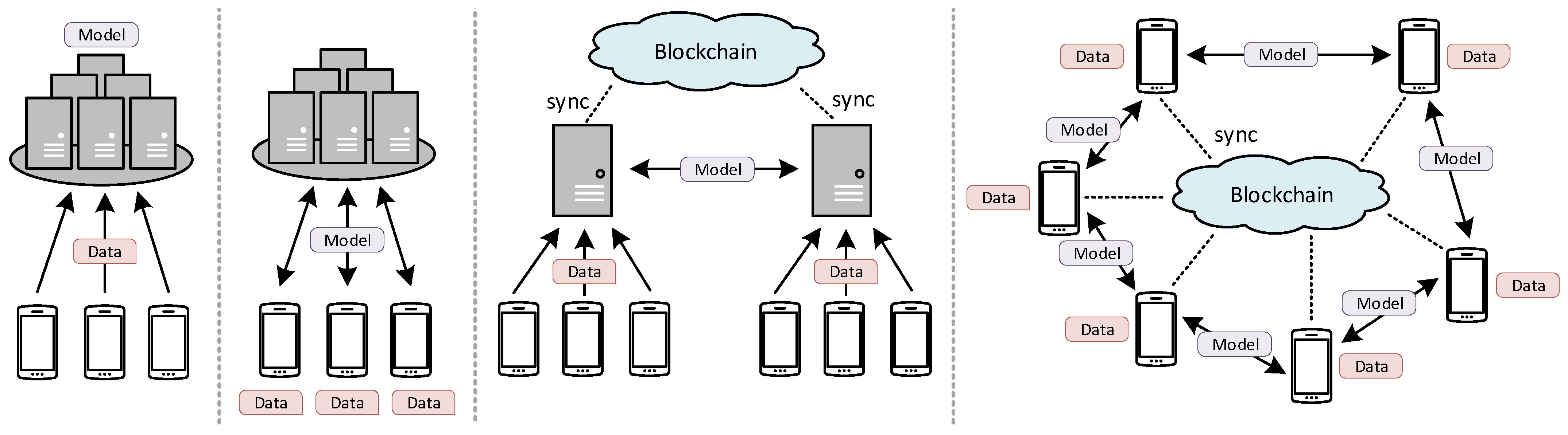
Trustworthy Federated Learning: A Survey
Improved lattice enumeration algorithms by primal and dual
FIBPRO: Peer-to-peer data management and sharing cloud storage
Security Analysis of End-to-End Encryption for Zoom Meetings⋆
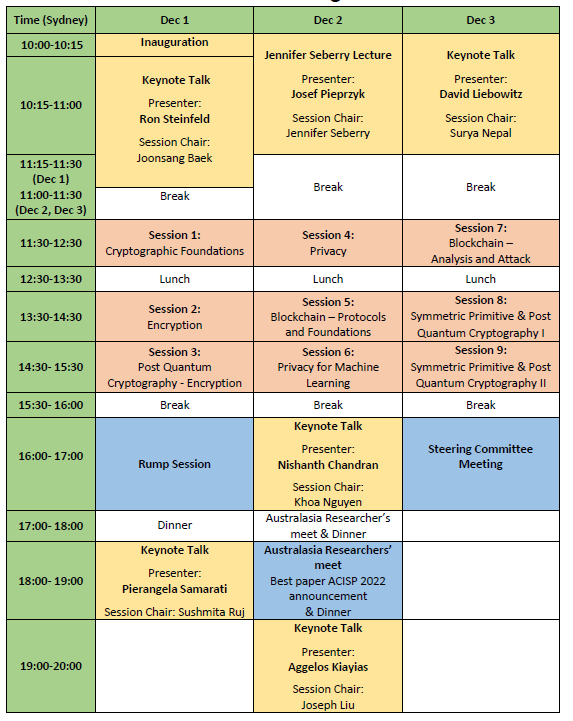
Conference Program
Quantum‐resistant anonymous identity‐based encryption with trable
Applied Sciences | Free Full-Text | Analyzing the Threats to
ACISP 2021 - The 26th Australasian Conference on Information
FVF-AKA: A Formal Verification Framework of AKA Protocols for
A survey of state-of-the-art sharding blockchains: Models
ACS Event
Advances in Cyber Security: Principle, Techniques, and Applications
FIBPRO: Peer-to-peer data management and sharing cloud storage
Trustworthy Federated Learning: A Survey
PDF) PIRB: Privacy-Preserving Identity-Based Redactable
Applied Sciences | Free Full-Text | Analyzing the Threats to
Detecting Audio Adversarial Examples in Automatic Speech
Improved lattice enumeration algorithms by primal and dual
Security Analysis of End-to-End Encryption for Zoom Meetings
A survey of state-of-the-art sharding blockchains: Models
Prof. L. Jean Camp EDUCATION EMPLOYMENT & APPOINTMENTS
FVF-AKA: A Formal Verification Framework of AKA Protocols for
FIBPRO: Peer-to-peer data management and sharing cloud storage
Trustworthy Federated Learning: A Survey
Status Report on the Final Round of the NIST Lightweight
Sensors | Free Full-Text | Blockchain-Based Federated Learning
Detecting Audio Adversarial Examples in Automatic Speech
Authentication Technologies For Cloud Computing, IoT and Big Data
Home | Acisp24
商品の情報
メルカリ安心への取り組み
お金は事務局に支払われ、評価後に振り込まれます
出品者
スピード発送
この出品者は平均24時間以内に発送しています